Safety researcher Yohanes Nugroho has launched a decryptor for the Linux variant of Akira ransomware, which makes use of GPU energy to retrieve the decryption key and unlock information at no cost.
Nugroho developed the decryptor after being requested for assist from a buddy, deeming the encrypted system solvable inside per week, based mostly on how Akira generates encryption keys utilizing timestamps.
The challenge ended up taking three weeks as a consequence of unexpected complexities, and the researcher spent $1,200 on GPU assets to crack the encryption key, however ultimately, he succeeded.
Utilizing GPUs to brute drive keys
Nugroho’s decryptor doesn’t work like a conventional decryption instrument the place customers provide a key to unlock their information.
As a substitute, it brute-forces encryption keys (distinctive for every file) by exploiting the truth that the Akira encryptor generates its encryption keys based mostly on the present time (in nanoseconds) as a seed.
An encryption seed is knowledge used with cryptographic features to generate sturdy, unpredictable encryption keys. Because the seed influences the important thing era, retaining it secret is essential to stop attackers from recreating encryption or decryption keys by way of brute drive or different cryptographic assaults.
Akira ransomware dynamically generates distinctive encryption keys for every file utilizing 4 totally different timestamp seeds with nanosecond precision and hashes by way of 1,500 rounds of SHA-256.
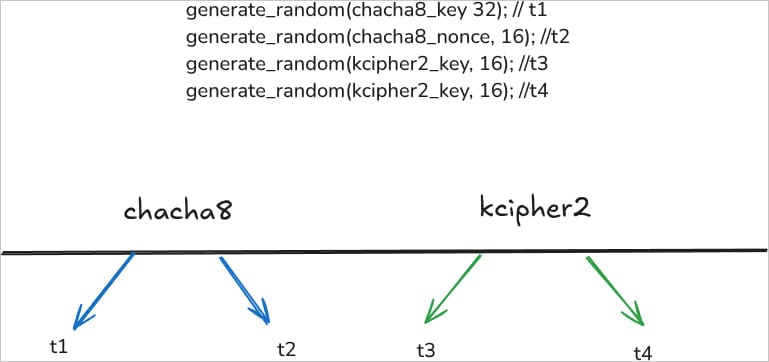
Supply: tinyhack.com
These keys are encrypted with RSA-4096 and appended on the finish of every encrypted file, so decrypting them with out the non-public secret is exhausting.
The extent of timing precision within the timestamps creates over a billion doable values per second, making it tough to brute drive the keys.
Additionally, Nugroho says that Akira ransomware on Linux encrypts a number of information concurrently utilizing multi-threading, making it exhausting to find out the timestamp used and including additional complexity.
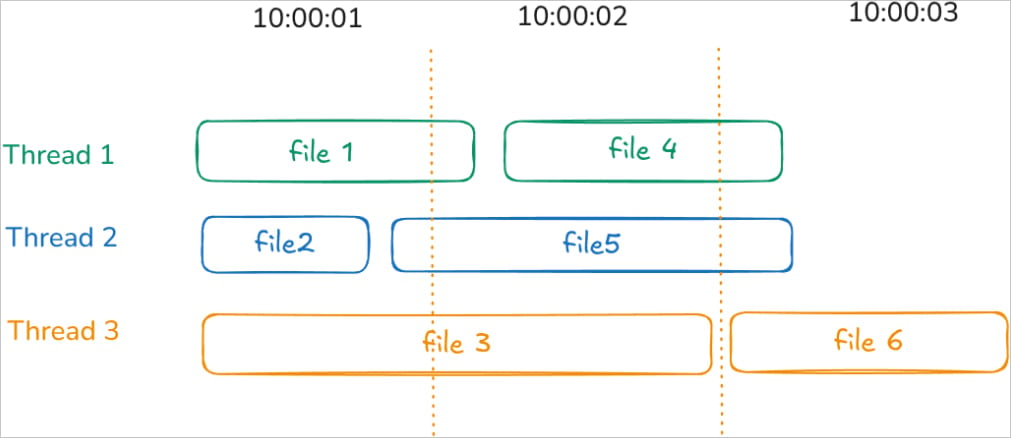
Supply: tinyhack.com
The researcher narrowed down the doable timestamps to brute-force by log information shared by his buddy. This allowed him to see when the ransomware was executed, the file metadata to estimate the encryption completion instances, and produce encryption benchmarks on totally different {hardware} to create predictable profiles.
Preliminary makes an attempt utilizing an RTX 3060 had been far too sluggish, with a ceiling of solely 60 million encryption assessments per second. Upgrading to an RTC 3090 did not assist a lot both.
Finally, the researcher turned to utilizing RunPod & Huge.ai cloud GPU providers that provided sufficient energy on the proper worth to verify the effectiveness of his instrument.
Particularly, he used sixteen RTX 4090 GPUs to brute-force the decryption key in roughly 10 hours. Nevertheless, relying on the quantity of encrypted information that want restoration, the method could take a few days.
The researcher famous in his write-up that GPU specialists may nonetheless optimize his code, so efficiency can possible be improved.
Nugroho has made the decryptor out there on GitHub, with directions on methods to recuperate Akira-encrypted information.
As all the time, when making an attempt to decrypt information, make a backup of the unique encrypted information, as there is a chance that information could be corrupted if the incorrect decryption secret is used.
BleepingComputer has not examined the instrument and can’t assure its security or effectiveness, so use it at your individual danger.


