A brand new instrument referred to as ‘Defendnot’ can disable Microsoft Defender on Home windows units by registering a faux antivirus product, even when no actual AV is put in.
The trick makes use of an undocumented Home windows Safety Heart (WSC) API that antivirus software program makes use of to inform Home windows it’s put in and is now managing the real-time safety for the gadget.
When an antivirus program is registered, Home windows robotically disables Microsoft Defender to keep away from conflicts from operating a number of safety purposes on the identical gadget.
The Defendnot instrument, created by researcher es3n1n, abuses this API by registering a faux antivirus product that meets all of Home windows’ validation checks.
The instrument is predicated on a earlier challenge referred to as no-defender, which used code from a third-party antivirus product to spoof registration with WSC. That earlier instrument was pulled from GitHub after the seller filed a DMCA takedown.
“Then, after a number of weeks after the discharge, the challenge blew up fairly a bit and gained ~1.5k stars, after that the builders of the antivirus I used to be utilizing filed a DMCA takedown request and I did not actually need to do something with that so simply erased all the things and referred to as it a day,” the developer explains in a weblog publish.
Defendnot avoids copyright points by constructing the performance from scratch by way of a dummy antivirus DLL.
Usually, WSC API is safeguarded by way of Protected Course of Gentle (PPL), legitimate digital signatures, and different options.
To bypass these necessities, Defendnot injects its DLL right into a system course of, Taskmgr.exe, that’s signed and already trusted by Microsoft. From inside that course of, it will possibly register the dummy antivirus with a spoofed show title.
As soon as registered, Microsoft Defender instantly shuts itself off, leaving no energetic safety on the gadget.
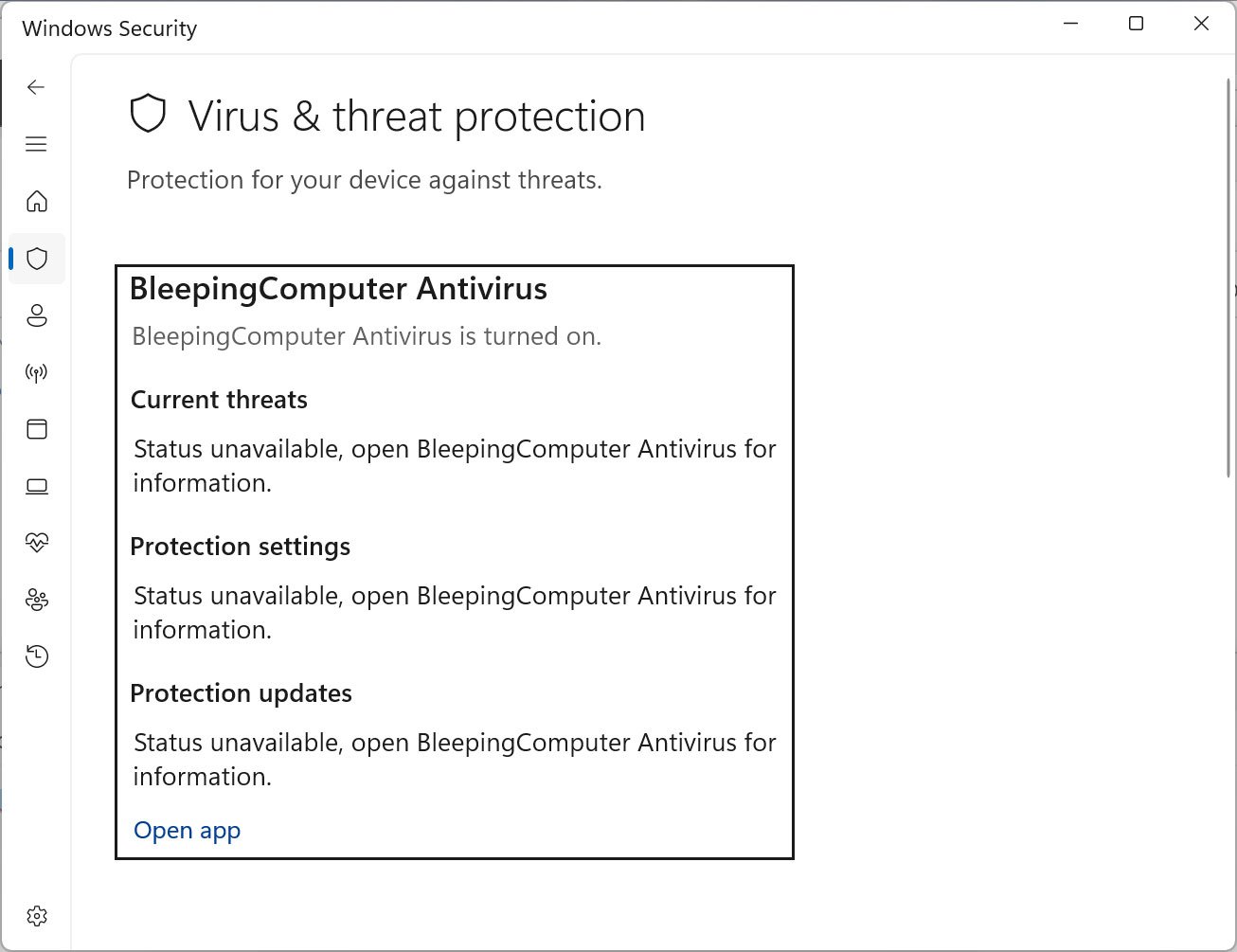
Supply: BleepingComputer
The instrument additionally features a loader that passes configuration information through a ctx.bin file and allows you to set the antivirus title you need to use, flip off registration, and allow verbose logging.
For persistence, Defendnot creates an autorun by way of the Home windows Process Scheduler in order that it begins once you log in to Home windows.
Whereas Defendnot is taken into account a analysis challenge, the instrument demonstrates how trusted system options may be manipulated to show off safety features.
Microsoft Defender is at the moment detecting and quarantining Defendnot as a ‘Win32/Sabsik.FL.!ml; detection.


