Coinbase has mounted a complicated bug in its account exercise logs that brought on customers to suppose their credentials have been compromised.
As BleepingComputer first reported earlier this month, Coinbase had mistakenly labeled failed login makes an attempt with incorrect passwords as two-factor authentication failues within the Account Exercise logs.
When a risk actor tried to entry somebody’s account and used the incorrect password, error messages stating “second_factor_failure” or “2-step verification failed” could be proven as a substitute.
These entries suggest {that a} legitimate username and password have been entered, however the log in was blocked by 2-factor authentication, resembling getting into the incorrect one-time passcode from an authenticator app.
Quite a few Coinbase customers contacted BleepingComputer with considerations that Coinbase had been breached as their passwords have been distinctive to the positioning, there was no signal of malware, and no different accounts have been affected.
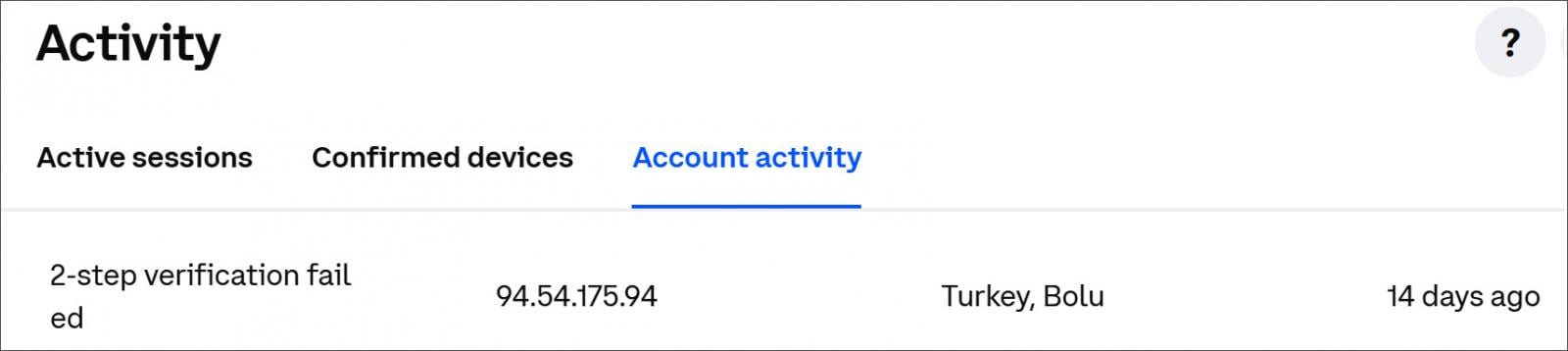
Nonetheless, Coinbase confirmed to BleepingComputer that its logging system was incorrectly attributing login makes an attempt with incorrect passwords as “2FA failures,” though the attackers had not efficiently reached the 2FA stage.
Coinbase has now pushed an replace to repair this incorrect labeling in order that “Password try failed” logs are proven in Account Exercise as a substitute.
Bugs like this are important to repair as they trigger pointless panic, with customers telling BleepingComputer that that they had reset all of their passwords and spent hours making an attempt to find out if their units have been compromsed on account of this bug.
These mislabeled entries might have additionally been utilized in social engineering assaults to persuade customers their account credentials have been compromised, doubtlessly permitting risk actors to achieve delicate data.
Risk actors generally goal Coinbase prospects in social engineering assaults to achieve entry to their accounts and drain the saved cryptocurrency.
BleepingComputer was informed that risk actors used these mislabeled error messages as a part of such assaults however couldn’t independently confirm if that was true.
Nonetheless, ongoing campaigns use automated SMS phishing (smishing) assaults and voice calls to impersonate Coinbase and try to steal 2FA tokens or credentials, so all customers needs to be cautious.
Coinbase has mentioned previously that they are going to by no means name prospects or ship textual content messages requesting they alter passwords or reset two-factor authentication and that prospects ought to deal with all such messages as scams.

