Google is rolling out a change to Chromium that “de-elevates” Google Chrome so it doesn’t run as an administrator to extend safety in Home windows.
Microsoft beforehand launched an identical function in 2019 to the Edge Browser. When customers launched Edge with elevated permissions, a warning would seem, recommending that they relaunch the browser with out administrative rights.
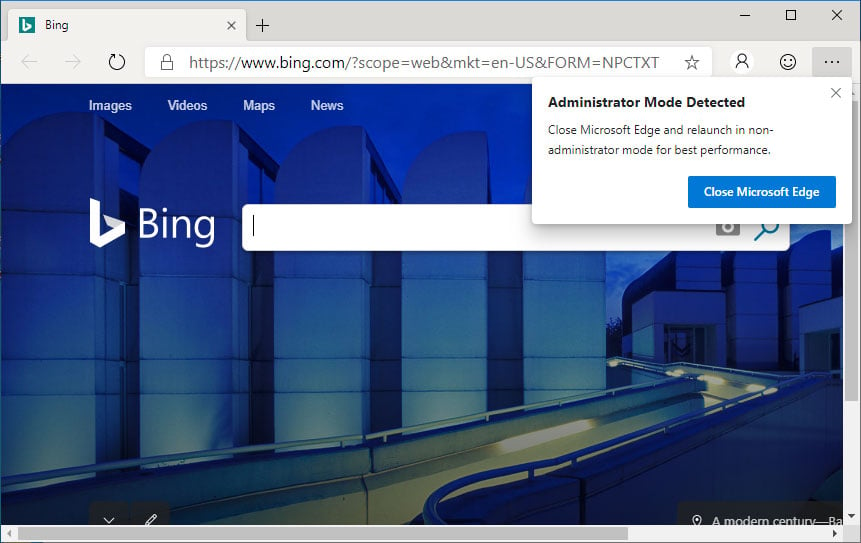
Later, Microsoft modified the function to robotically forestall the Edge browser from launching with elevated permissions.
Microsoft is now bringing the identical enhancements to Chromium, with builders submitting a commit to the Chromium supply code.
As noticed by Leo on X, Microsoft has confirmed that Chrome will now robotically de-elevate when customers attempt to launch it with elevated permissions.
“Mechanically de-elevate customers launching chrome elevated. This CL is predicated on adjustments we have had in Edge, circa 2019, which makes an attempt to robotically de-elevate the browser when it is run with the elevated a part of a cut up / linked token,” Stefan Smolen, who works with the Microsoft Edge group, wrote in a Chromium commit.
“This robotically makes an attempt a relaunch as soon as, after which if it nonetheless fails it falls again to the present behaviour (which tries to launch admin).”
Microsoft has additionally added a command-line swap, “-do-not-de-elevate,” to forestall the de-elevation after an auto-relaunch to forestall infinite loops.
” Don’t de-elevate the browser on launch. Used after de-elevating to forestall infinite loops,” reads a remark within the supply code.
This function doesn’t work for Chrome processes launched with elevated rights when in automation mode, in order to not intervene with instruments that will must run robotically.
Nevertheless, normally, Microsoft warns that launching the browser in admin mode is just not a good suggestion.
When Chrome runs as an Administrator, it inherits elevated permissions, which implies something you obtain and open by the browser may even launch with Administrator rights, which may pose a critical safety threat.
Should you by accident obtain and run a malicious file, it might execute with full system entry, probably compromising your complete working system with none warning.


