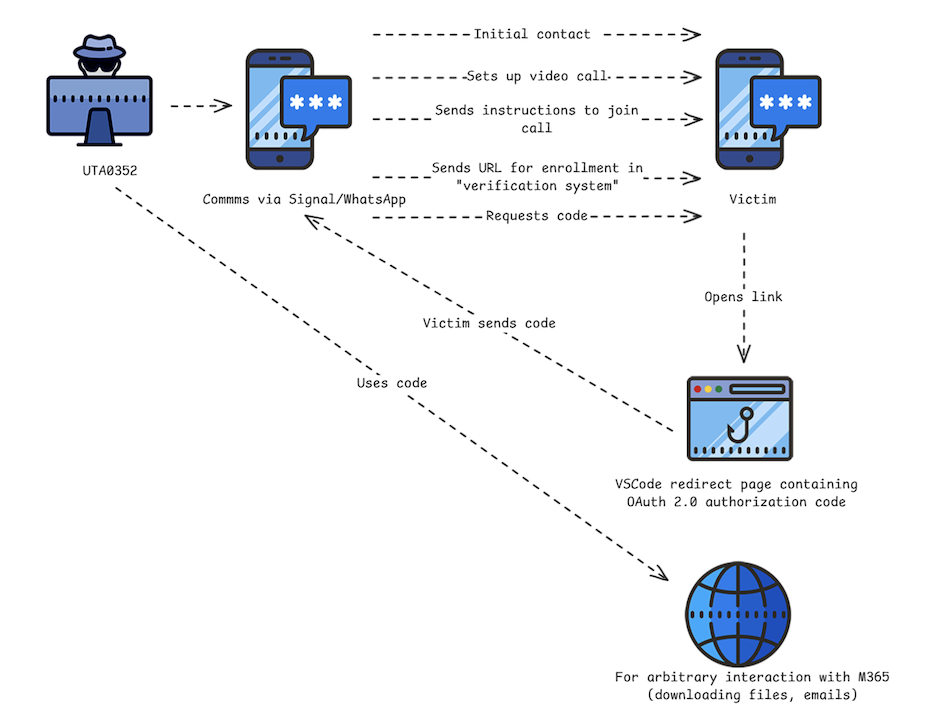
Russian menace actors have been abusing professional OAuth 2.0 authentication workflows to hijack Microsoft 365 accounts of staff of organizations associated to Ukraine and human rights.
The adversary is impersonating officers from European nations and phone targets via WhatsApp and Sign messaging platforms. The aim is to persuade potential victims to supply Microsoft authorization codes that give entry to accounts, or to click on on malicious hyperlinks that gather logins and one-time entry codes.
Cybersecurity firm Volexity noticed this exercise since early March, proper after the same operation, reported in February by Volexity and Microsoft, that used Gadget Code Authentication phishing to steal Microsoft 365 accounts.
Volexity tracks the menace actors chargeable for the 2 campaigns as UTA0352 and UTA0355 and asesses with medium confidence that they’re each Russian.
Assault circulation
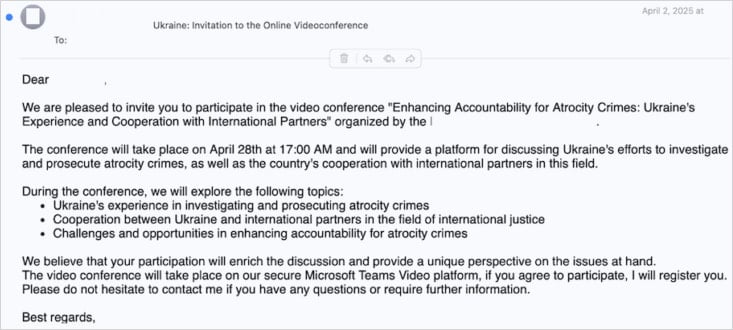
In a report printed as we speak, the researchers describe the assault as beginning with a message over Sign or WhatsApp. Volexity notes that in a single case the communication got here from a compromised Ukrainian authorities account.
Supply: Volexity
The attacker impersonate European political officers or Ukrainian diplomats and lure targets with invites to non-public video conferences to debate Ukraine-related affairs.
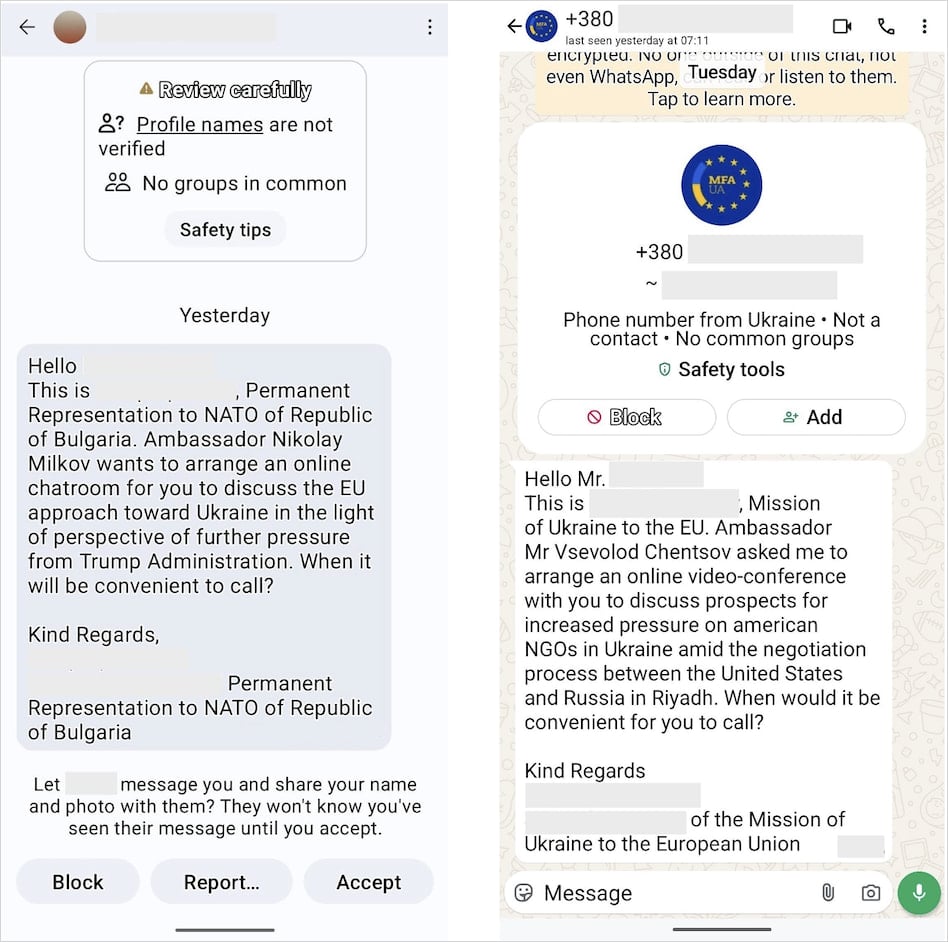
As soon as the communication channel established, the attacker sends an OAuth phishing URL underneath the pretext that it’s required for becoming a member of the video name.
Supply: Volexity
UTA0352 might share directions to affix the assembly within the type of a PDF file together with a malicious URL crafted to log the consumer into Microsoft and third-party apps that use Microsoft 365 OAuth workflows.
After the goal authenticates, they’re “redirected to an in-browser model of Visible Studio Code, hosted at insiders.vscode.dev,” the researchers clarify.
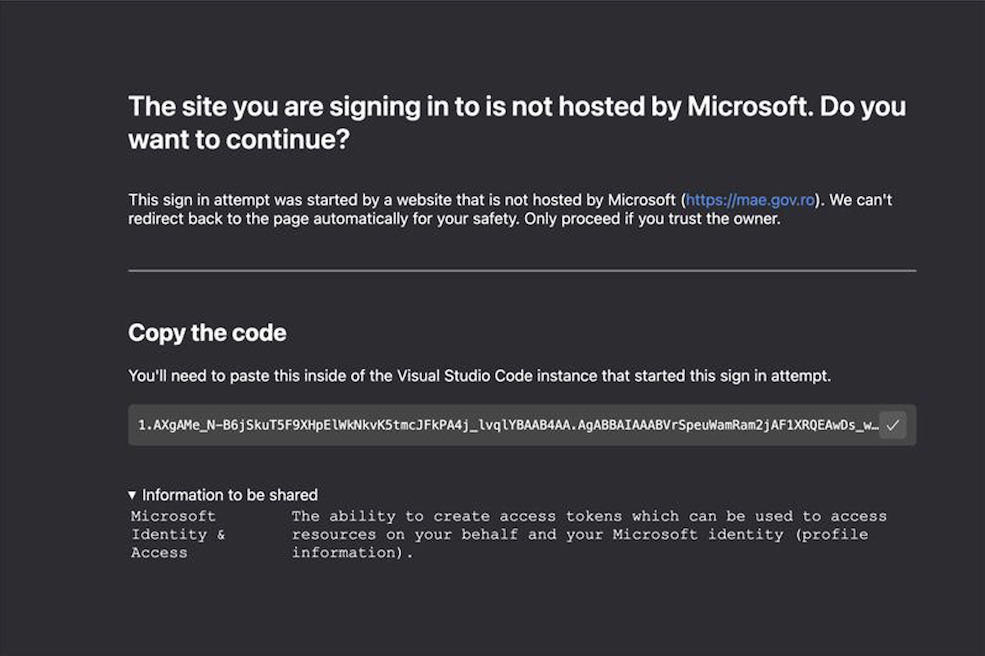
The touchdown web page can obtain login paramenters from Microsoft 365, which incorporates OAuth and the goal will see the dialog beneath:
Supply: Volexity
Utilizing social engineering, the attacker tries to trick the sufferer to ship again the code above, underneath the pretense that it’s wanted to affix the assembly.
Nevertheless, the string is an authorization code legitimate for 60 days that can be utilized to acquire an entry token for “all sources usually obtainable to the consumer.”
“It must be famous that this code additionally appeared as a part of the URI within the deal with bar. The Visible Studio Code seems to have been set as much as make it simpler to extract and share this code, whereas most different situations would merely result in clean pages,” Volexity says.
The researchers simplified within the following diagram the assault circulation focusing on customers by counting on a Visible Studio Code first-party utility:
Supply: Volexity
The analysis be aware that there are older variations of the latest phishing assault, the place the attacker used a format for the AzureAD v1.0 as an alternative of the v2.0, the variations consisting within the URL parameters used.
The marketing campaign in April attributed to UTA0355 is much like that of UTA0352 however the preliminary communication got here from a compromised Ukrainian authorities e mail account and the attacker used the “stolen OAuth authorization code to register a brand new system to the sufferer’s Microsoft Entra ID (previously Azure Energetic Listing).”
Volexity researchers say that when the system registered, they needed to persuade the goal to approve the two-factor authentication (2FA) request to have the ability to entry the sufferer’s e mail.
To attain that, the menace actor social-engineered their method by saying that the 2FA code was essential to “acquire entry to a SharePoint occasion related to the convention.”
This ultimate step offers the attacker a token to entry the sufferer’s info and emails, but in addition a newly registered system to keep up unauthorized entry for an extended interval.
“In logs reviewed by Volexity, preliminary system registration was profitable shortly after interacting with the attacker. Entry to e mail information occurring the next day, which was when UTA0355 had engineered a scenario the place their 2FA request can be authorized,” Volexity researchers say.
To guard in opposition to such assaults, Volexity advises organising alerts on logins utilizing the Visible Studio Code client_id, block entry to ‘insiders.vscode.dev’ and ‘vscode-redirect.azurewebsites.internet’.
The researchers additionally suggest organising conditional entry insurance policies to restrict entry to authorized units solely.

