An lively marketing campaign from a risk actor doubtlessly linked to Russia is focusing on Microsoft 365 accounts of people at organizations of curiosity utilizing system code phishing.
The targets are within the authorities, NGO, IT providers and expertise, protection, telecommunications, well being, and vitality/oil and fuel sectors in Europe, North America, Africa, and the Center East.
Microsoft Risk Intelligence Heart tracks the risk actors behind the system code phishing marketing campaign as ‘Storm-237’, Primarily based on pursuits, victimology, and tradecraft, the researchers have medium confidence that the exercise is related to a nation-state operation that aligns with Russia’s pursuits.
System code phishing assaults
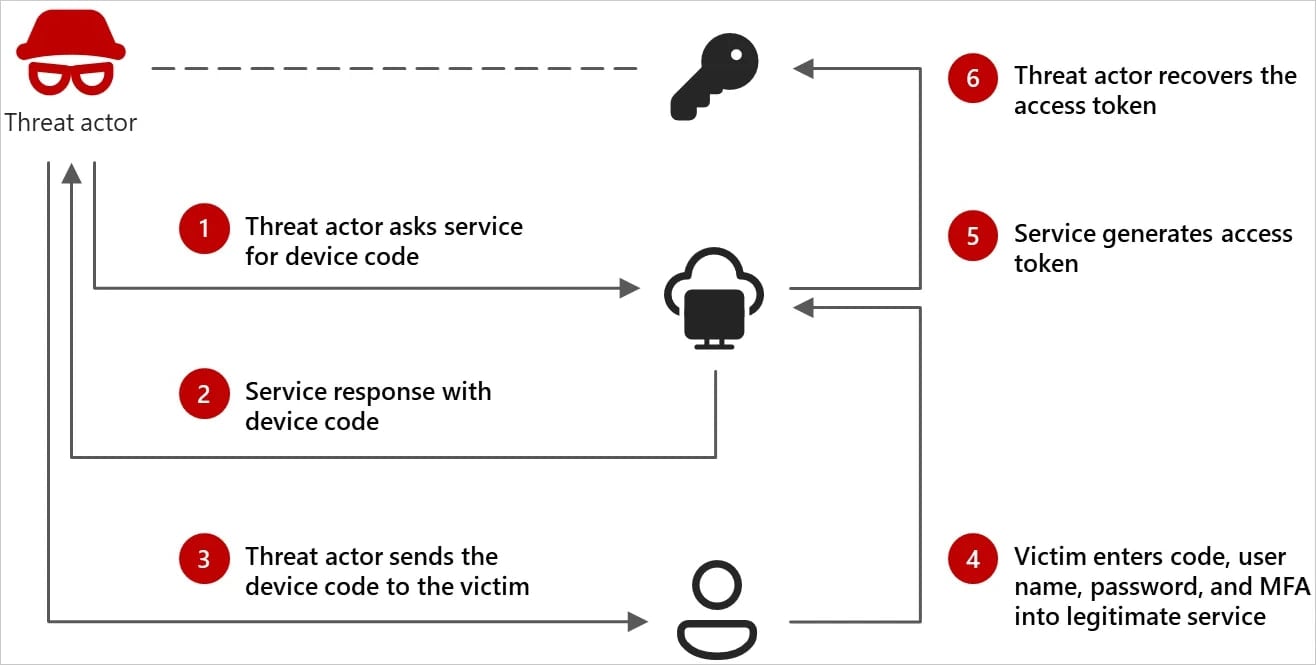
Enter constrained units – those who lack keyboard or browser assist, like sensible TVs and a few IoTs, depend on a code authentication move to permit permitting customers to signal into an software by typing an authorization code on a separate system like a smartphone or laptop.
Microsoft researchers found that since final August, Storm-2372 abuses this authentication move by tricking customers into getting into attacker-generated system codes on official sign-in pages.
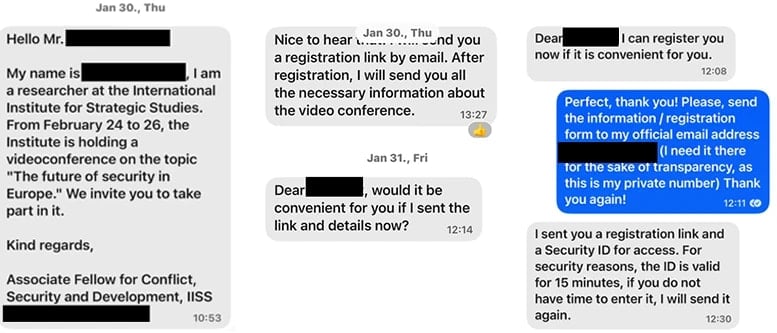
The operatives provoke the assault after first establishing a reference to the goal by “falsely posing as a outstanding individual related to the goal” over messaging platforms like WhatsApp, Sign, and Microsoft Groups.
Supply: Microsoft
The risk actor step by step establishes a rapport earlier than sending a pretend on-line assembly invitation by way of e-mail or message.
In accordance with the researchers, sufferer receives a Groups assembly invite that features a system code generated by the attacker.
“The invites lure the consumer into finishing a tool code authentication request emulating the expertise of the messaging service, which offers Storm-2372 preliminary entry to sufferer accounts and allows Graph API knowledge assortment actions, akin to e-mail harvesting,” Microsoft says.
This offers the hackers entry to the sufferer’s Microsoft providers (e-mail, cloud storage) without having a password for so long as the stolen tokens stay legitimate.
Supply: Microsoft
Nevertheless, Microsoft says that the attacker is now utilizing the particular shopper ID for Microsoft Authentication Dealer within the system code sign-in move, which permits them to generate new tokens.
This opens new assault and persistence possiblities because the risk actor can use the shopper ID to register units to Entra ID, Microsoft’s cloud-based identification and entry administration resolution.
“With the identical refresh token and the brand new system identification, Storm-2372 is ready to receive a Major Refresh Token (PRT) and entry a corporation’s sources. We’ve got noticed Storm-2372 utilizing the linked system to gather emails” – Microsoft
Defending towards Storm-2372
To counter system code phishing assaults utilized by Storm-2372, Microsoft proposes blocking system code move the place potential and imposing Conditional Entry insurance policies in Microsoft Entra ID to restrict its use to trusted units or networks.
If system code phishing is suspected, instantly revoke the consumer’s refresh tokens utilizing ‘revokeSignInSessions’ and set a Conditional Entry Coverage to drive re-authentication for affected customers.
Lastly, use Microsoft Entra ID’s sign-in logs to observe for, and rapidly determine excessive volumes of authentication makes an attempt in a brief interval, system code logins from unrecognized IPs, and sudden prompts for system code authentication despatched to a number of customers.

