Cybercriminals are exploiting a trick to show off Apple iMessage’s built-in phishing safety for a textual content and trick customers into re-enabling disabled phishing hyperlinks.
With a lot of our each day actions performed from our cellular units, whether or not paying payments, purchasing, or speaking with mates and colleagues, menace actors more and more conduct smishing (SMS phishing) assaults towards cellular numbers.
To guard customers from such assaults, Apple iMessage mechanically disables hyperlinks in messages acquired from unknown senders, whether or not that be an e-mail tackle or telephone quantity.
Nevertheless, Apple instructed BleepingComputer that if a person replies to that message or provides the sender to their contact listing, the hyperlinks will likely be enabled.
Tricking customers into replying
Over the previous couple of months, BleepingComputer has seen a surge in smishing assaults that try and trick customers into replying to a textual content in order that hyperlinks are enabled once more.
As you possibly can see under, a faux USPS delivery difficulty and a faux unpaid street toll textual content have been despatched from unknown senders, and iMessage mechanically disabled the hyperlinks.
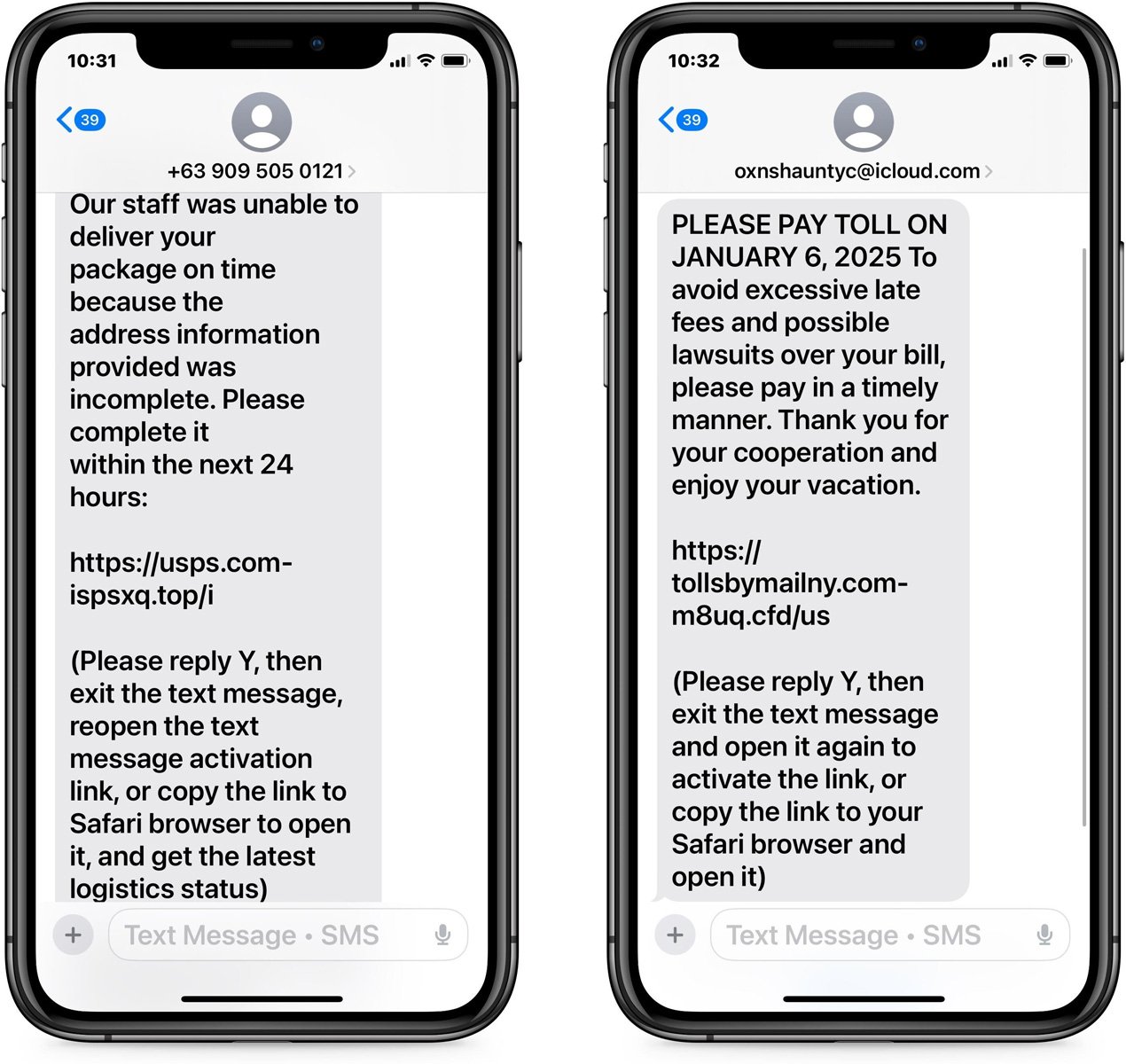
Supply: BleepingComputer
Whereas neither of those phishing lures is new, we observed that these smishing texts, and others seen just lately, ask customers to answer with “Y” to allow the hyperlink.
“Please reply Y, then exit the textual content message, reopen the textual content message activation hyperlink, or copy the hyperlink to Safari browser to open it,” reads the smishing messages.
Additional analysis exhibits this tactic has been used over the previous yr, with a surge because the summer season.
As customers have turn out to be used to typing STOP, Sure, or NO to substantiate appointments or decide out of textual content messages, the menace actors are hoping this acquainted act will lead the textual content recipient to answer to the textual content and allow the hyperlinks.
Doing so will allow the hyperlinks once more and switch off iMessage’s built-in phishing safety for this textual content.
Even when a person would not click on on the now-enabled hyperlink, the act of replying tells the menace actor that they now have a goal that responds to phishing texts, making them a much bigger goal.
Whereas most of our common readers will have the ability to spot that these are phishing assaults, BleepingComputer was proven one of many above texts by an older household pal, who was uncertain if it was official.
Sadly, these kind of individuals are generally the goal of these kind of phishing messages, main them to enter their private info, bank card info, or different particulars that the attackers then steal.
When you obtain a message whose hyperlinks are disabled or from an unknown sender asking you to answer to the textual content, you’re strongly suggested not to take action.
As a substitute, contact the corporate or group on to confirm the textual content and ask if there may be anything you must do.

