The Arkana Safety extortion gang briefly listed over the weekend what seemed to be newly stolen Ticketmaster knowledge however is as an alternative the info stolen throughout the 2024 Snowflake knowledge theft assaults.
The extortion group posted screenshots of the allegedly stolen knowledge, promoting over 569 GB of Ticketmaster knowledge on the market, inflicting hypothesis that this was a brand new breach.
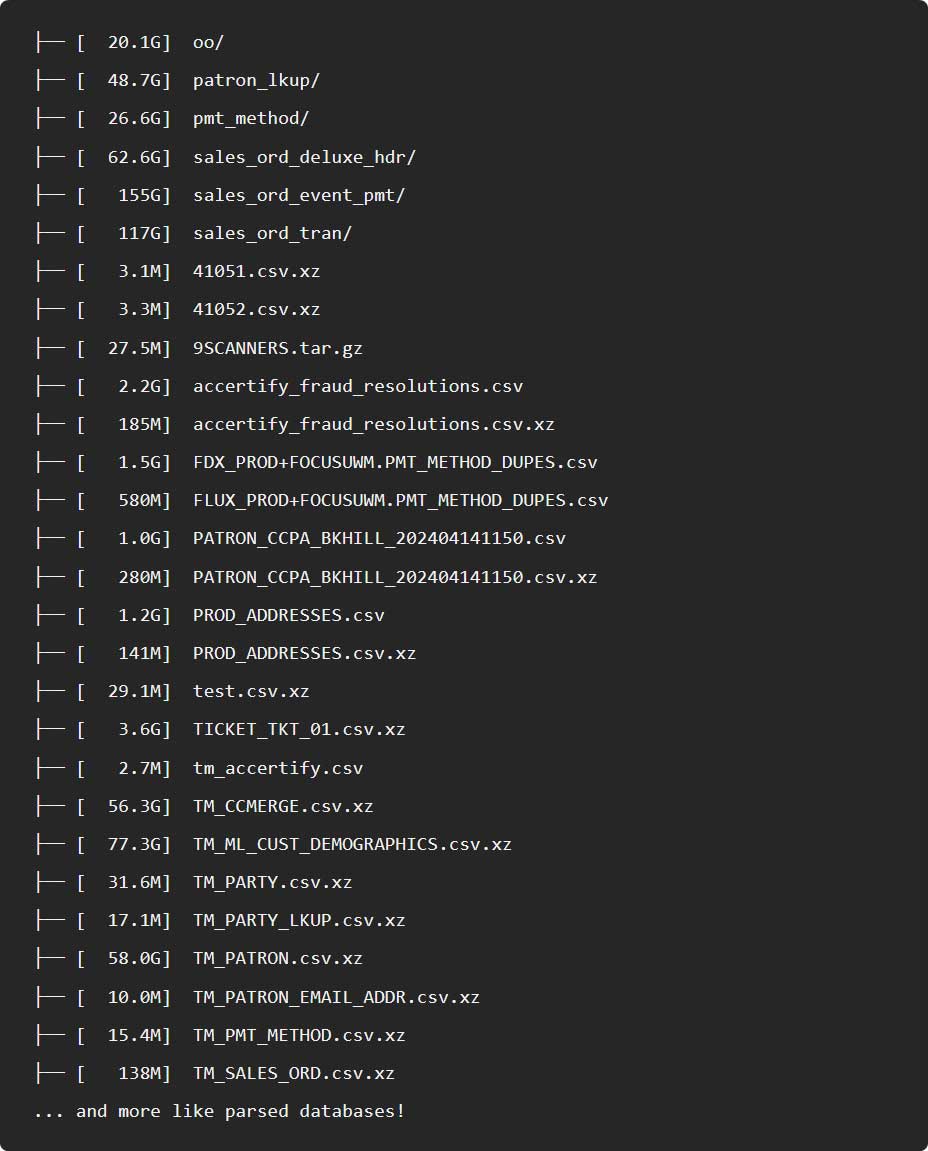
Supply: BleepingComputer
Nevertheless, BleepingComputer has decided that the information proven within the Arkana publish match samples of Ticketmaster knowledge we beforehand noticed throughout the 2024 Snowflake knowledge theft assaults.
Moreover, one of many photographs had the caption “rapeflaked copy 4 fast sale 1 purchaser,” which is a reference to a software named “RapeFlake.”
RapeFlake is a customized software created by the menace actors to carry out reconnaissance and exfiltrate knowledge from Snowflake’s databases.
As beforehand reported, the Snowflake assaults focused many organizations, together with Santander, Ticketmaster, AT&T, Advance Auto Components, Neiman Marcus, Los Angeles Unified, Pure Storage, and Cylance. These assaults have been claimed by an extortion group referred to as ShinyHunters.
These assaults have been performed utilizing compromised Snowflake credentials stolen by infostealers, which have been then used to obtain firm knowledge to be used in extortion schemes.
Ticketmaster was among the many most generally extorted victims within the Snowflake assault, which led to the theft of private and ticketing info. After the info was supplied on the market on-line, the corporate confirmed the breach on the finish of Could and started notifying affected clients.
Following the preliminary leak, the menace actors ramped up their extortion makes an attempt by releasing what they claimed have been print-at-home tickets and even alleged Taylor Swift tickets in a collection of posts on a hacking discussion board.
Whereas Arkana didn’t specify the origin of the info, using Snowflake references and the file names matching beforehand leaked information signifies that the group was trying to resell previous stolen knowledge.
Whether or not or not Arkana beforehand bought this knowledge, whether or not the group is made up of menace actors who beforehand had the info, or whether or not they’re working with ShinyHunters to promote it’s unclear.
On June 9, the entry for the Ticketmaster knowledge had been faraway from the Arkana Safety knowledge leak web site.
The title “ShinyHunters” has been linked to a lot of breaches through the years, together with the huge PowerSchool knowledge breach the place knowledge was stolen for 62.4 million college students and 9.5 million lecturers for six,505 college districts throughout the U.S., Canada, and different international locations.
Extra just lately, Mandiant tied ShinyHunters to a current marketing campaign concentrating on Salesforce accounts, the place menace actors have been breaching accounts to steal buyer knowledge and extort firms.
As quite a few menace actors tied to ShinyHunters have been arrested over the previous three years [1, 2, 3], it’s unclear if that is the unique group or different menace actors claiming to be them to throw off regulation enforcement.
BleepingComputer contacted Arkana and Ticketmaster relating to the itemizing however didn’t obtain a response.


